Many companies use standard consumer-grade VPNs for business purposes. Typically, they are unaware of corporate-focused solutions and/or want to cut costs. In either case, this is a conceptual mistake that can jeopardize company data and reputation. The differences between a VPN for personal use and a dedicated platform for businesses are not just in price but in the service’s very DNA—its architecture, management capabilities, scalability, and ability to meet security regulations. What are the key distinctions between the two, and which features are absolutely essential?

Why Isn’t a Consumer VPN Enough?
While it might seem that a VPN is just a VPN, the reality of a business deployment demands something entirely different from personal use. A personal VPN might be able to protect an individual, but a corporate platform must handle the protection of the entire organization. What features should it not lack?
- Centralized management and consistent control: A unified control panel/dashboard that allows administrators to manage all users, licenses, servers, and enforce security policies across the entire organization5.
- Scalability and access management:
- Quickly and easily add new users (ideally without disrupting the billing cycle).
- Lifecycle automation (provisioning) and detailed access rights control for each team and individual through defined roles—for example, via integration with systems like Azure AD, Okta, and Google Workspace14.
- Robust security for all: A company does not rely on individuals to configure their VPNs correctly. It enforces and ensures consistent security for everyone, including Device Posture Monitoring, which prevents access from risky agents2.
- Auditing and compliance: Tools and activity logs that enable and document everything necessary for audits, certifications, and achieving compliance with standards like GDPR, HIPAA, PCI-DSS, or ISO 270014.
- Advanced networking: Businesses need to connect specific branches, certain devices, or grant access to sensitive systems only from specific IPs and devices. This requires features like Site-to-Site VPN, dedicated IP addresses, and their whitelisting2.
Such features are not only completely absent in consumer VPNs but are often incompletely implemented even in services marketed as “business-grade” solutions.
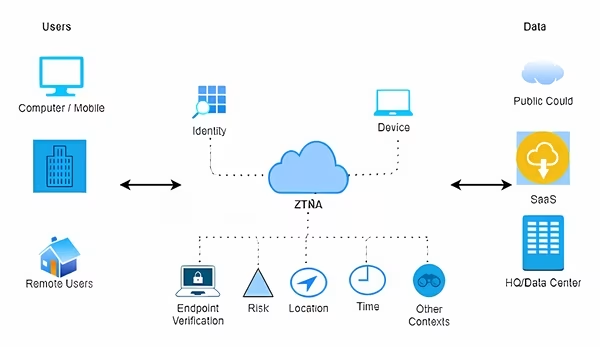
Zero Trust Network Access Diagram (Source: ResearchGate)
What Capabilities Should a Business VPN Have?
There are several business plans on the market. Let’s showcase the potential functionalities using NordLayer as an example, as it covers the most ground:
1. Zero Trust Network Access (ZTNA)
The classic approach to security considered the administrator as the default user, granting them all rights and then trimming them down. In contrast, the modern Zero Trust principle starts with the assumption that every request comes from an unauthorized external agent. It grants only the permissions that are strictly necessary for a specific user, and every access request is verified, regardless of its origin.
The implementation of Zero Trust Network Access is a fundamental point where a secure corporate VPN differs from a personal one—and even distinguishes NordLayer16 from its competitors. After connecting to a server, the latter implicitly trust the user and no longer limit their permissions or verify subsequent requests.
NordLayer goes even further and adds the following to ZTNA:
- Device Posture Monitoring: Actively checks if endpoints (laptops, mobiles) meet corporate security standards and restricts their access if they don’t.2
- Biometric and Multi-Factor Authentication (MFA): Enhances login security beyond a simple password.2
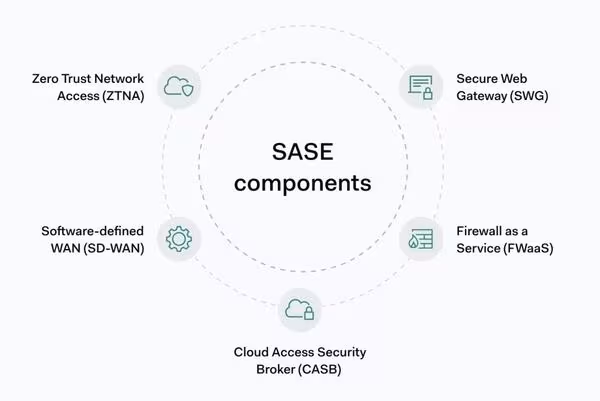
Key Components of SASE Architecture (Source: NordLayer)
2. Cloud Firewall (FWaaS) and SASE
Here, NordLayer definitively sets itself apart from the competition and moves beyond the “business VPN” category. The platform is built on a SASE (Secure Access Service Edge) architecture, which is a direct response to the dissolution of the traditional corporate perimeter.21 In an era where users and corporate data are scattered across the globe, protecting the headquarters is no longer enough: security must follow each user, wherever they are.
A key pillar of the SASE architecture is the integrated Cloud Firewall (FWaaS) . Unlike cumbersome and expensive hardware firewalls that guard physical offices, NordLayer provides a firewall as a service directly from the cloud. This means:
- Policies for everyone, everywhere: The administrator sets security policies in a central panel, and they are instantly and consistently applied to every user, whether they work from home, a coffee shop, or a branch on the other side of the world20.
- Enforces a “Default-Deny” principle: In line with the Zero Trust philosophy, the Cloud Firewall blocks all traffic by default. Access is granted only based on explicitly defined rules that administrators can granularly set for specific teams, gateways, and destination resources (IP addresses)20.
- Security at the network edge: Traffic is filtered before it even reaches user devices. This creates a first line of defense that protects the entire network, not just individual endpoints.
In practice, NordLayer provides more than just an encrypted tunnel; it offers a complete, centrally managed security zone that replaces complex and outdated infrastructure. It’s a strategic shift from reactive defense to proactive network access control.
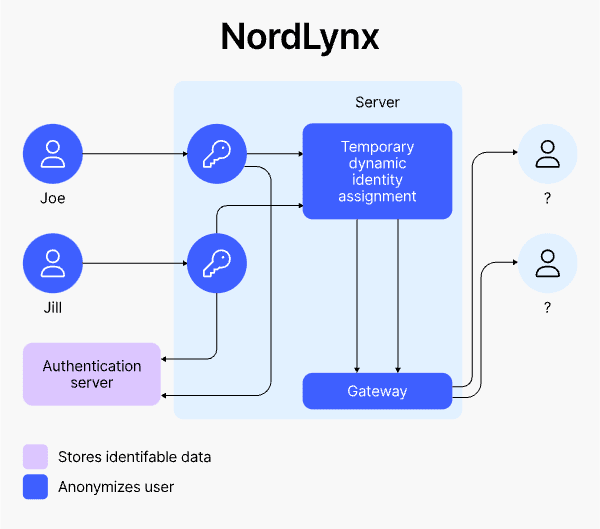
NordLynx adds a double NAT system and temporary dynamic identities to WireGuard, preventing the storage of user IPs or identities—thus eliminating a privacy weakness in WireGuard (Source: NordVPN)
3. NordLynx and Other Security and Management Features
Companies will appreciate not only the comprehensive security but also the features directly related to organizational management or arising from having a distributed team across many locations:
- Deep Packet Inspection (DPI): NordLayer analyzes the content of network traffic itself to identify and block unauthorized applications or outdated, risky protocols.5 This is a proactive protection that goes far beyond the basic DNS filtering offered by competitors.
- Centralized Management and Automation: An intuitive control panel allows for managing users, licenses, and security policies from one place. Key to this is the support for SCIM for automated user provisioning and integration with identity providers like Azure AD, Okta, Google Workspace, and OneLogin14. Surfshark completely lacks this level of automation, and Proton VPN offers only limited support7, 8.
- NordLynx Protocol: While many use WireGuard, NordLayer has implemented its own enhanced version—NordLynx.10 Thanks to its double NAT (Network Address Translation) system, it provides the top-tier speed of the WireGuard protocol without needing to store identifiable user data on the server, which increases privacy and security10.
- Site-to-Site and Smart Remote Access: Easily connect entire office networks or create a virtual LAN for secure remote access to devices, as if everyone were in the same room2.
Direct Comparison: NordLayer vs. Competitors
| Feature | NordLayer | Proton VPN Business | Surfshark for Teams |
|---|---|---|---|
| Zero Trust Network Access | ✅ | ❌ | ❌ |
| Cloud Firewall (FWaaS) | ✅ | ❌ | ❌ |
| Deep Packet Inspection | ✅ | ❌ | ❌ |
| Site-to-Site VPN | ✅ | ❌ | ❌ |
| Device Posture Monitoring | ✅ | ❌ | ❌ |
| Integrations (SCIM, Azure AD, Okta) | ✅ | Limited | ❌ |
| Dedicated IP for Team | ✅ | ✅ | ❌ |
Weaknesses of Competitors from a Business Perspective
- Proton VPN for Business: Emphasizes privacy through its Swiss jurisdiction and Secure Core feature. However, it lacks key tools for enterprise-scale management and policy enforcement18. Its model is less flexible and lacks a comprehensive ZTNA/SASE architecture.
- Surfshark for Teams: Is essentially a consumer VPN with multi-account management capabilities.8 It tries to attract with a low price and unlimited connections—but at the cost of lacking any real enterprise features.19 It is missing ZTNA, dedicated IPs for teams, advanced networking, and meaningful integration with corporate systems. As a serious corporate security solution, it is completely inadequate.
Where is a Robust Business VPN Essential?
- Regulated industries subject to mandates like GDPR, HIPAA, NIS2, PCI DSS, or SOX.
- Sectors threatened by industrial espionage.
- Global companies with distributed teams, especially in high-risk countries.
NordLayer is a flexible and easily implementable cybersecurity tool for businesses of any size or work model.1
A Tailored Solution for Any Deployment?
The beauty of the NordLayer platform lies in its flexibility. It can adapt to the unique needs of different types of businesses.
Scenario 1: An Agile Freelancer or Small Team (up to 10 people)
Needs: Fast and seamless implementation, robust protection of client data, and easy management without requiring a dedicated IT department.
How NordLayer Helps:
- Deployment in minutes: As a fully cloud-based platform (SaaS), NordLayer enables setup without any hardware purchase. Thanks to the intuitive Control Panel, everything can be configured in less than 10 minutes.13
- Client data protection: With a dedicated IP address, you can securely access a client’s systems by having them whitelist your IP. AES-256 encryption and the NordLynx protocol ensure all communication is completely confidential.10
Scenario 2: A Company with International Branches
Needs: Secure and stable communication across geographically separate locations, a unified security policy, and compliance with local regulations in different countries.
How NordLayer Helps:
- Network interconnection: The Site-to-Site VPN feature creates a secure and encrypted bridge between all three branches and the cloud infrastructure. This allows all employees to share resources securely as if they were on the same network.2
- Compliance: NordLayer holds certifications like ISO 27001, SOC 2, and is GDPR compliant. For expansion into restrictive regions, it offers obfuscated servers that mask the very fact that a VPN is being used, helping to bypass local firewalls and censorship.4
Scenario 3: A Handler of Sensitive Data (Healthcare, Finance)
Needs: The highest level of security, demonstrable auditability of all access, end-to-end encryption, and strict network segmentation to protect critical data.
How NordLayer Helps:
- Auditability and oversight: The platform provides detailed activity logs (audit logs) that precisely record who accessed what and when. This is crucial for meeting standards like HIPAA (healthcare) or PCI-DSS (finance).4
- Impenetrable protection: The Zero Trust architecture ensures that only authenticated users from verified devices can access sensitive data.16 Granular network segmentation using the Cloud Firewall and dedicated servers allows for creating a completely isolated and fortified environment for the most critical data.11
Why Not Just Assemble Your Own Solution?
- Management complexity: Outages, operational issues, administrative and security risks.
- Lack of integration: Deficiencies in synchronization and connection with internal and external systems, and the use of Shadow IT unprotected by a VPN, ZTNA, or SASE.
- Legal liability for data breaches, non-compliance, loss of certifications, and reputational damage.
Pricing
NordLayer offers transparent and scalable pricing plans, starting at $8 per user/month (Lite plan)3. Although the base price may seem higher than Surfshark’s, NordLayer integrates the functionality of multiple enterprise and security products—not just a consumer VPN. Therefore, it can actually save the customer up to 65% in Total Cost of Ownership (TCO).13
A custom price quote is available for 50 or more users.

The Choice for a Business VPN?
In the current market, it’s difficult to speak of a real choice for a business VPN. Surfshark offers only the illusion of a corporate solution at a low price, while Proton VPN focuses on a narrow niche of maximum privacy, but only for individuals or small teams with IT security experts—lacking requirements for centralized management and security.
And we are only talking about the most common alternatives. Players with marginal market coverage (HMA, Twingate, Perimeter 81, ExpressVPN) are in an even worse position. That leaves only:
List of references
- NordLayer: Network security platform for business. Available at: https://nordlayer.com/
- Secure your business network with advanced features | NordLayer. Available at: https://nordlayer.com/features/
- Network security plans & pricing | NordLayer. Available at: https://nordlayer.com/pricing/
- Security Compliance solutions for your business | NordLayer. Available at: https://nordlayer.com/security-compliance/
- NordLayer review – TechRadar. Available at: https://www.techradar.com/reviews/nordlayer
- Secure business VPN for small and enterprise companies | Proton… Available at: https://proton.me/business/vpn
- Proton VPN business plans explained | Proton VPN. Available at: https://protonvpn.com/support/proton-vpn-business
- Best VPN for teams – Surfshark. Available at: https://surfshark.com/for-teams
- The best VPNs for businesses and teams of 2025: Expert tested | ZDNET. Available at: https://www.zdnet.com/article/best-vpns-for-businesses-and-teams/
- Surfshark vs. NordVPN: Which is the best VPN for you in 2025? | NordVPN. Available at: https://nordvpn.com/blog/surfshark-vs-nordvpn/
- Features in review: Cloud Firewall | NordLayer. Available at: https://nordlayer.com/blog/features-in-review-cloud-firewall/
- Unlock your network security potential with NordLayer’s comprehensive solution. Available at: https://hudsonweekly.com/unlock-your-network-security-potential-with-nordlayers-comprehensive-solution/
- NordLayer: Cybersecurity SaaS for Growing Businesses | Technology Magazine. Available at: https://technologymagazine.com/articles/nordlayer-review-comprehensive-cybersecurity-for-businesses
- Combine NordLayer with SCIM User Management | NordLayer Blog. Available at: https://nordlayer.com/blog/nordlayer-with-scim-user-management/
- The Best VPNs for Small Business 2025 | All About Cookies. Available at: https://allaboutcookies.org/best-vpn-for-small-business
- What is NordLayer? Available at: https://nordlayer.com/what-is-nordlayer/
- The Best VPN for Business and Enterprise in 2025. Available at: https://www.vpnmentor.com/blog/best-vpns-businesses/
- Proton Business VPN – TechRadar. Available at: https://www.techradar.com/pro/software-services/proton-business-vpn
- Surfshark VPN features: advanced online security – Surfshark. Available at: https://surfshark.com/features
- Secure business network access with Cloud Firewall | NordLayer. Available at: https://nordlayer.com/features/cloud-firewall/
- Protect your business network with SASE solution | NordLayer. Available at: https://nordlayer.com/sase/
Additional Resources
- Ajish, Deepa. (2024). The significance of artificial intelligence in zero trust technologies: a comprehensive review. Journal of Electrical Systems and Information Technology. 11. 10.1186/s43067-024-00155-z. Available at ResearchGate.com
SEO specialista a copywriter Daniel Beránek: expert na výkonově orientované SEO, Local Business SEO, datový a technický copywriting a budování brandu.
Odborné know-how a zkušenosti:
komunikace a psychologie: Mgr. psychologie, Mgr. žurnalistiky a komunikačních studií, novinářská praxe
SEO, weby, síťařina: vlastní praxe od 2013, každodenní práce s WP aj. CMS, webdesign, technická optimalizace vč. výběru webserverů, úprav .htaccess, výběru hostingu a CDN aj.
IT security: několik let přispívání pro SOOM.cz: portálu o IT security a hackingu + zaměření i na IT security v další novinářské praxi
e-commerce: příprava měsíčníku Novinky e-commerce pro eshop developera Shopsys, vlastní copywriting a SEO pro eshopy
retail: vybudování, provoz, osobní prodej a všechny ostatní aktivity v rámci maloobchodních prodejen pro bratra, vlastní retail: opakovaná účast na vánočních trzích – viz. Vánoční trhy: marže a umění prodat tisíckrát jinak